Cloud security is one of the most pressing concerns for organizations across the world, especially as businesses continue to move critical workloads and data to the cloud. As cloud computing evolves, ensuring the security of cloud infrastructure, services, and data is paramount. Cyber threats are more sophisticated than ever, and data breaches can result in […]
What Are The Best Practices For Ensuring Data Protection In 2025?
As we move further into the digital age, ensuring data protection becomes more critical than ever. With advancements in technology, businesses, and individuals now rely heavily on digital systems to store, process, and transmit sensitive data. In 2025, data protection will evolve with increasing complexity, especially in response to the growing risks of cyberattacks, privacy […]
How Can Your Organization Ensure Cybersecurity Compliance?
In today’s digital age, organizations are increasingly vulnerable to cyber threats. With sensitive data being stored and shared online, cybersecurity has become a top priority for businesses of all sizes. One of the key components of a strong cybersecurity strategy is ensuring cybersecurity compliance, which refers to adhering to specific legal, regulatory, and industry standards […]
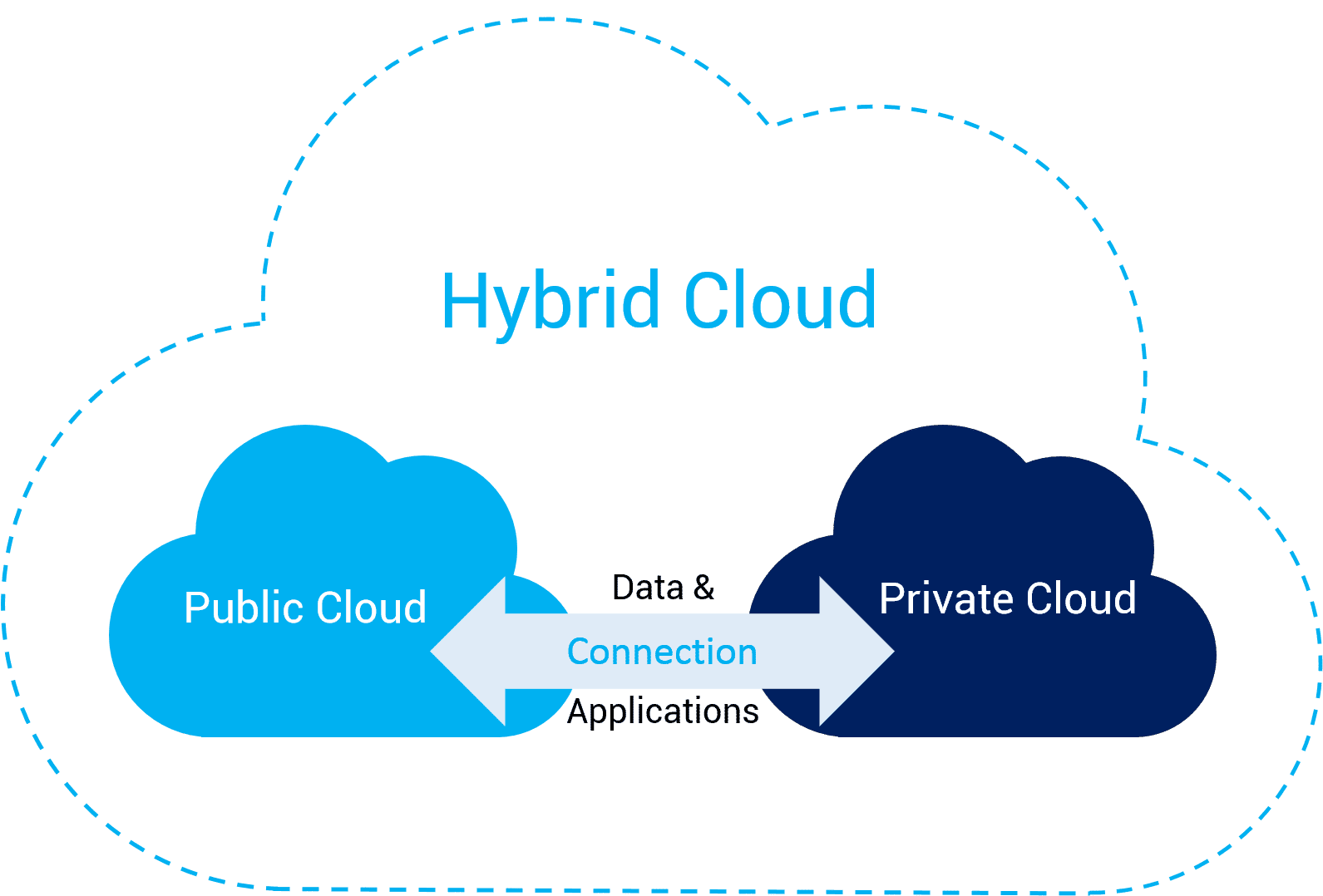
Why Is Hybrid Cloud The Future of IT Infrastructure?
In recent years, cloud computing has become a central element of digital transformation, helping organizations innovate and scale efficiently. With advancements in cloud technologies, businesses now have the flexibility to choose between public, private, or hybrid cloud solutions. Among these, the hybrid cloud has emerged as one of the most sought-after approaches for businesses looking […]
What Are The Best IT Security Practices For 2025?
In today’s rapidly evolving digital landscape, information security has become more important than ever. With each passing year, cyber threats grow more sophisticated, and the methods of attack become more diverse. As we look ahead to 2025, organizations and individuals must adopt robust IT security practices to stay ahead of cybercriminals. This article delves deep […]